DFIR4win - Automates the artifacts extraction
Manually extracting artefacts from an infected computer can sometimes be tedious with so much information to search for, documents and logs. That's why the less time it takes to extract the most relevant information, the longer we can spend looking for any clues or evidence.
With this idea in mind I found in Github a script that looked very good from the user AlrikRr (I invite you to take a look at his cool projects), specifically I'm talking about Forensic-Extract.
Looking at his project I thought "OK, it extracts very useful information and records, but... what if I add the option to extract hives?", so I took advantage of it and made a few more changes:
- Translated the code into English
- Optimised the code as much as I could
- Added the option to extract hives
- Added a Microsoft Defender status checker
You can see the project in my Github: b4shnhawx/DFIR4win
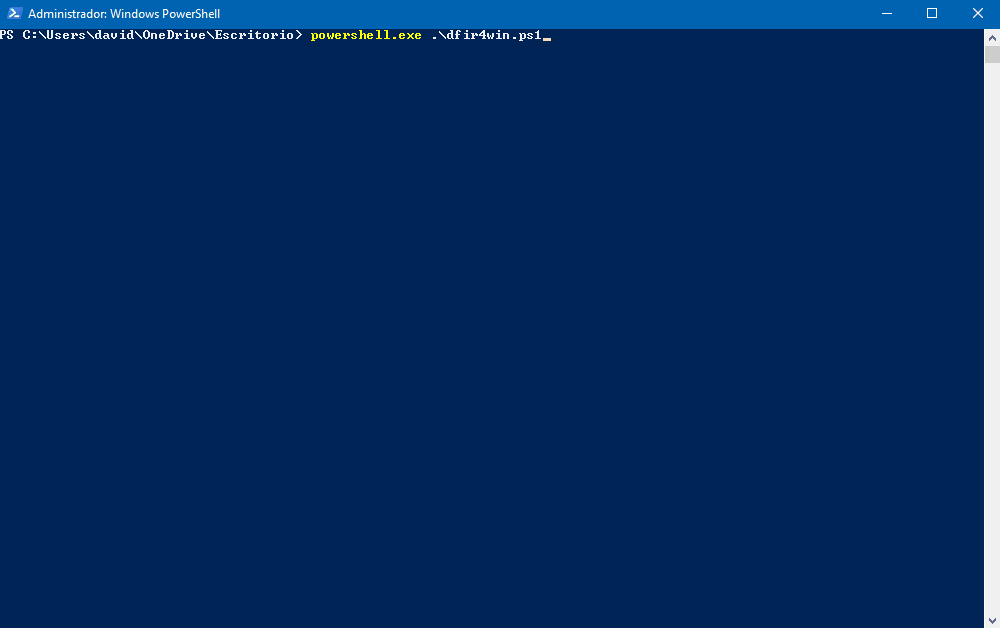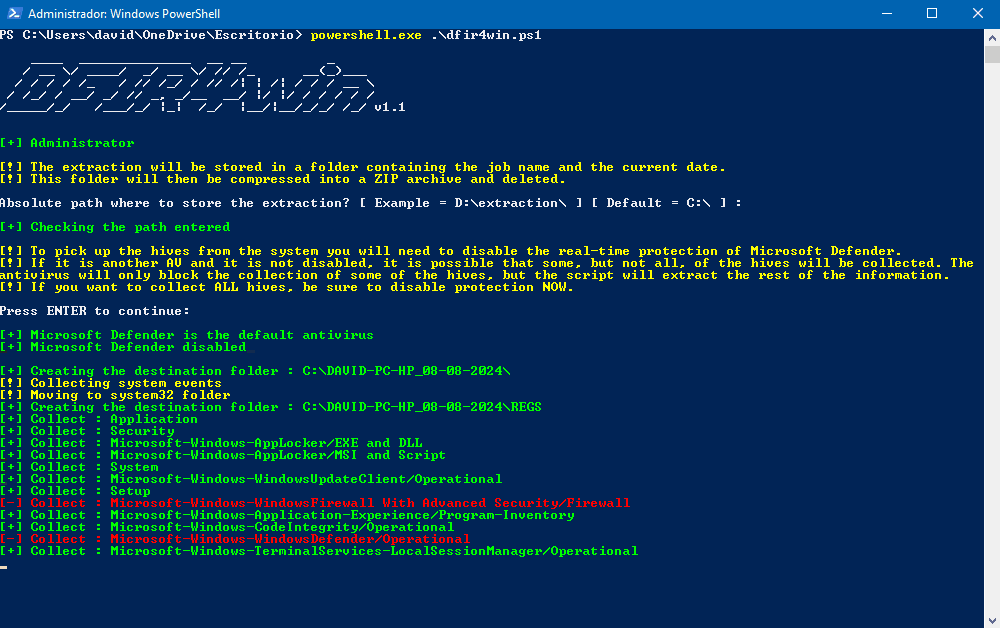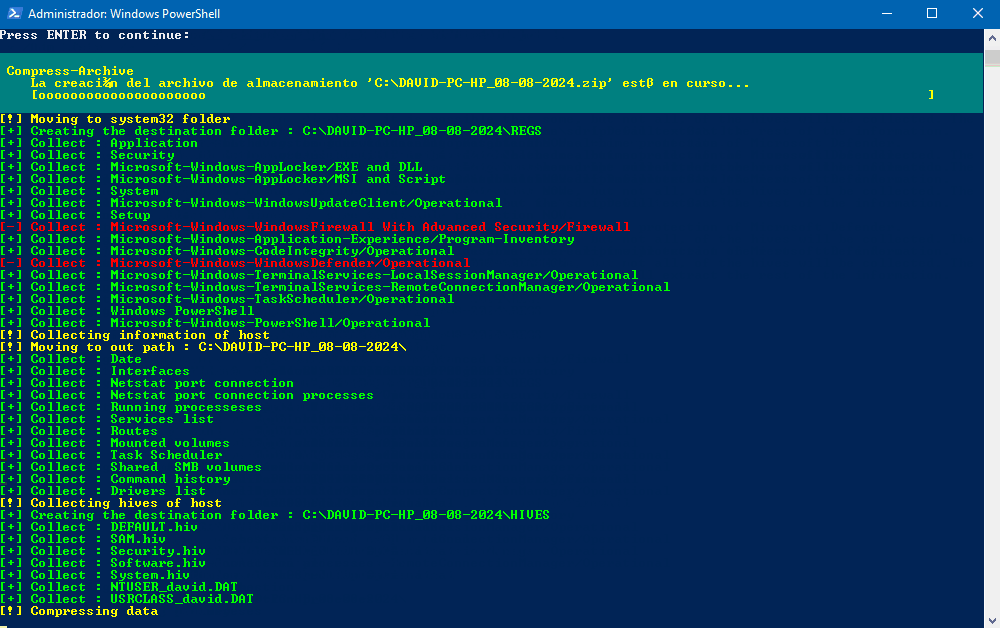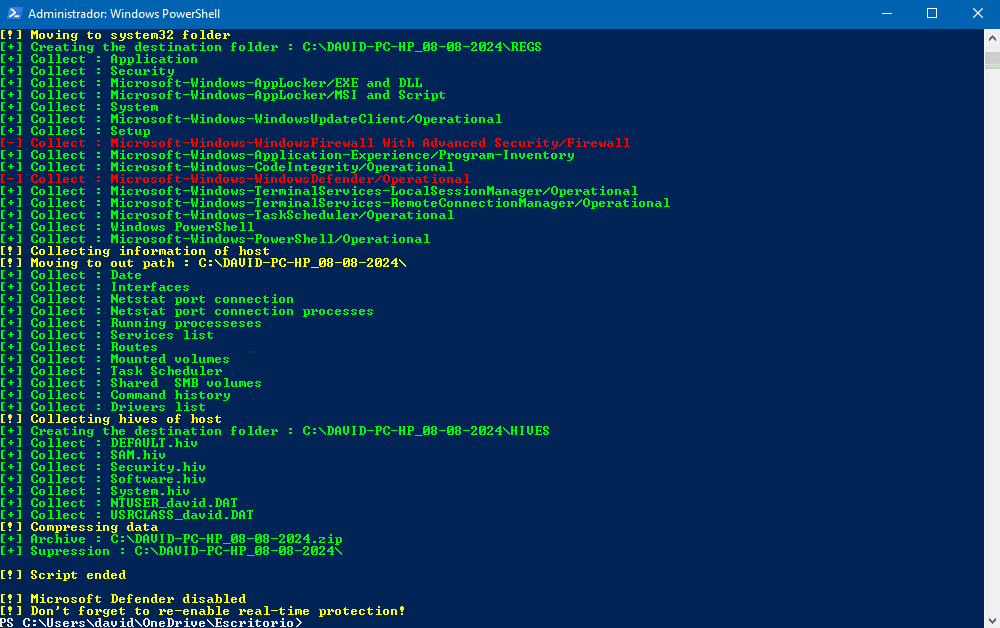
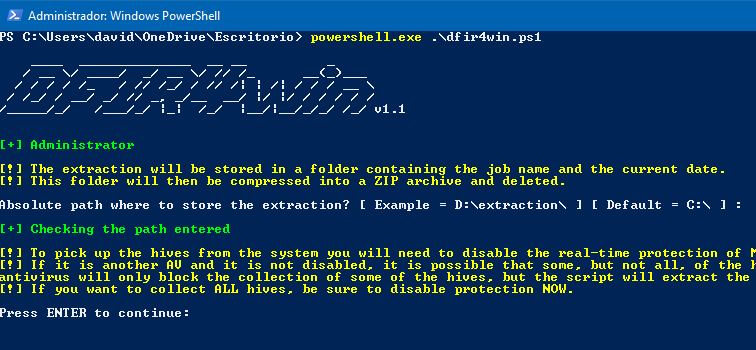
DFIR4win can automate the collection of most of the data you need to analyse activity on a Windows machine and compress it all into a ZIP file.
It includes:
- Relevant host information
- Event logs
- Log hives (for more details, see Microsoft documentation)
If you want to extract the hives, you may need to disable the real-time protection of your antivirus (AV), as it may consider the action suspicious. By default, Windows uses Windows Defender.
This script detects whether your active AV is Windows Defender or some other third-party antivirus. If it is the latter, it is possible that other modules of your AV are blocking the extraction of the files, so I recommend you to manually check if all the files you need have been extracted correctly.
If the script is not working properly to extract the files, you can do it manually with a program (such as Eric Zimmerman's Registry Explorer).
This would be the final directory tree:
./HOST_DD-MM-YYYY.zip
|
|-- REGS
| |-- *_HOST_DD-MM-YYYY.evtx
|
|-- HIVES
| |-- Security.hiv
| |-- SAM.hiv
| |-- DEFAULT.hiv
| |-- NTUSER_USERNAME.DAT
| |-- System.hiv
| |-- USRCLASS_USERNAME.DAT
| |-- Software.hiv
|
|-- Host-Info_HOST_DD-MM-YYYY.txt
You have all the information about how the script works in the repository 😁
Comments