SSH TelegramBot in Python
Today I bring you a project that I finished some time ago, but that has earned a place in my favourite projects: a bot for Telegram.
Ok, but what is the difference between this bot and any other ‘hello_world_telgrambot.py’ bot on the internet? Basically, this one is capable of interpreting commands on the machine that is running it (Linux) 💣
Before we throw our hands up in the air ‘Oh no, it's open to the internet and anyone can access it! Yes, that's true, and I know it, but that's why I've added a security measure that's as simple as it is reliable.
Each Telegram user has a unique ID, so let's use it to our advantage.
Raspberry Pi, in every message sent to the Telegram bot, compare the ID of the sender with the ones I have put in your whitelist. If the ID doesn't match, it's NOT me, so don't pay attention to it.
Although I have tried to make it plug-and-play, reducing a lot the necessary configuration to be able to replicate it to your liking, I want to mention several things here even though everything is explained in the comments in the code itself and its repository.
You can see the project in my Github: b4shnhawx/ssh-telegram-bot
UNDERSTANDING THE SCRIPT
First of all, please note that the following dependencies must be installed:
pip3 install telebot
pip3 install python-telegram-botI have divided the code into three parts. Mandatory, Optional and Main.
- Mandatory: As the name indicates, this part of the code is the minimum for the SSH bot to work.
In this section you only need to change the token of your bot, and the chat IDs you want to allow. You can put as many IDs as you want separated by commas in case you want multiple users to have access to the same machine......... ### ----------------------------------------------- ### --------- MANDATORY CODE FOR SSH BOT ---------- ### ----------------------------------------------- ### --- VARIABLES --- ........ token = "xxxxxxxxx:ABCDEFabcdef..." permit_chat_id = (CHAT_ID_1, CHAT_ID_2, CHAT_ID_3...) ........ - Optional: Here you can add or modify the existing options and functions as you wish. In my case, the options that I have added are ping_pc, public_ip, magic_packet_pc, suspend_pc MINUTOS, logoff_pc, shut_down_pc, cmd bash command.
In this section is where you should put the variables for your optional functions. In case you don't want any other optional functions, you can delete all the content up to the MAIN section......... ### ------------------------------------------------ ### -------- OPTIONAL FUNCTIONS FOR THE BOT -------- ### ------------------------------------------------ ### --- VARIABLES --- mac_magic_packet = "MAC_ADDRESS" ip_pc = "IP_ADDRESS" user = "USER" password = "PASSWORD" ........To add new functions, at the end of the optional functions I have left an example / template (called EXAMPLE COMMAND) to add other commands with arguments.
Don't forget that if you add new optional functions, you should add them in the MANDATORY section in the /start and /test commands so that they appear as help. - Main: It is the part that runs the bot, so it should not be changed.
USE CASE EXAMPLES
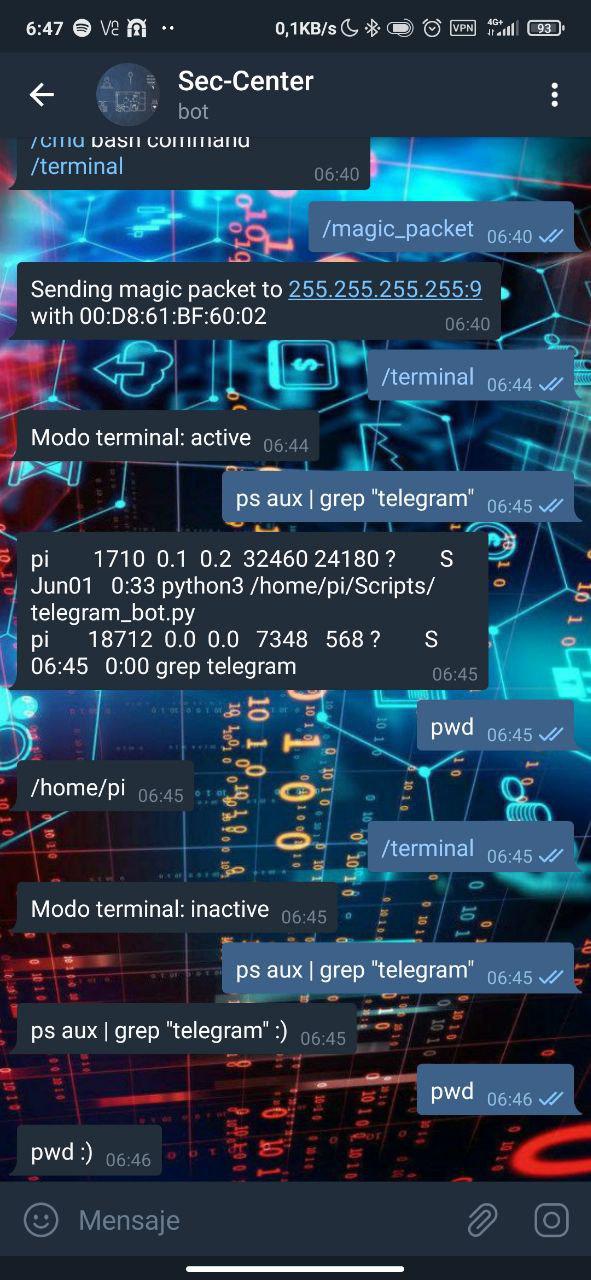
To enable and disable SSH mode, simply send the command /terminal. At this point, the bot will indicate the status of the terminal and if it is active, anything we send will be interpreted as a command and the output will be sent to us.
(Note that it has its limitations, so don't expect to do a ‘man ssh’ to work xD)
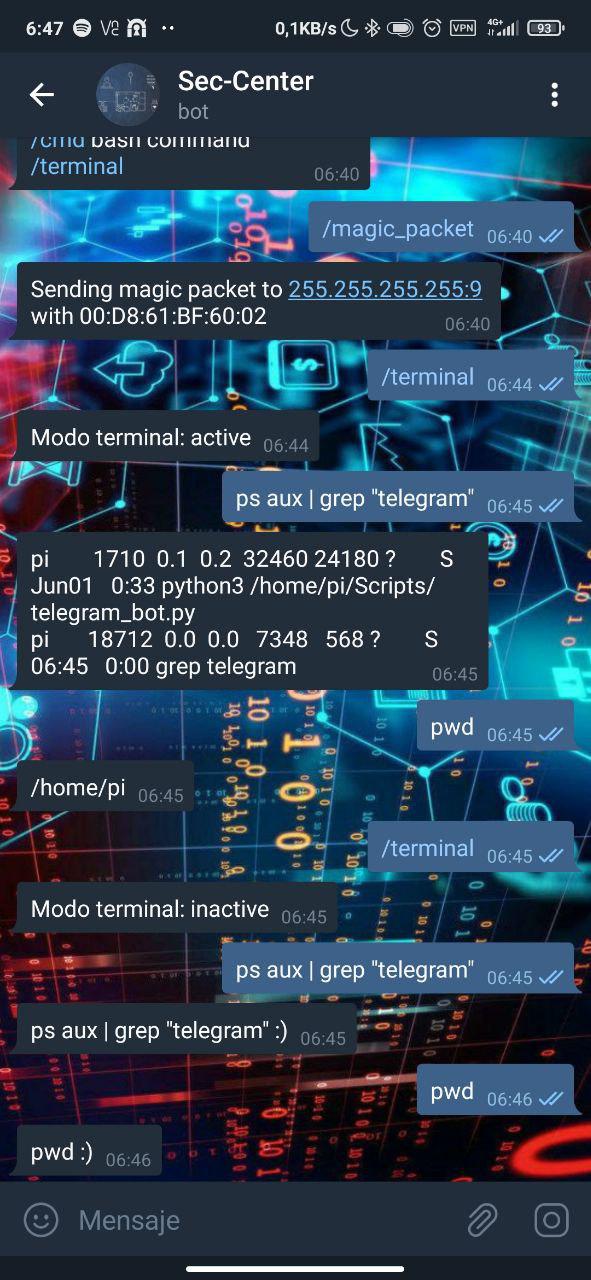
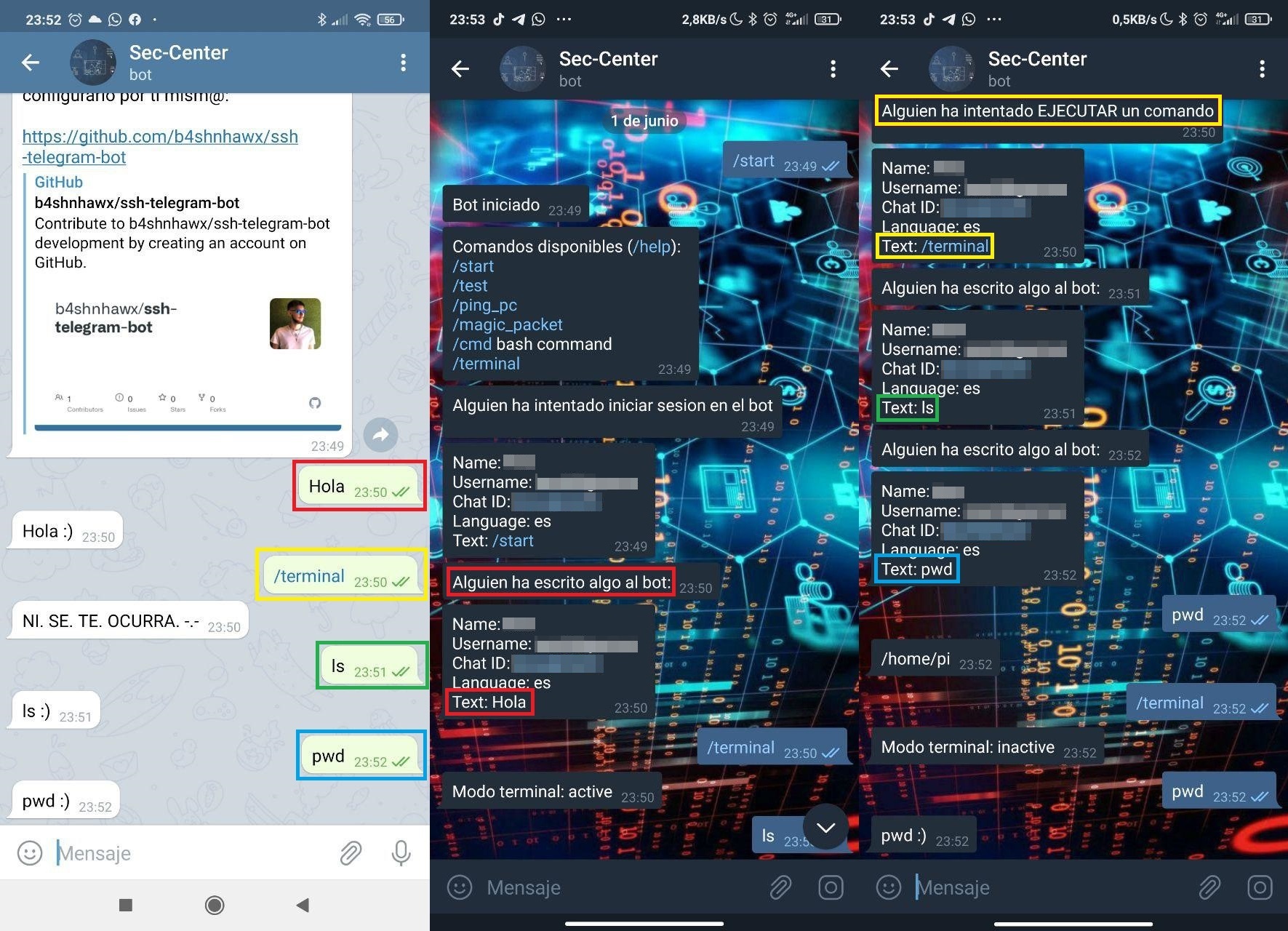
An example of an intrusion attempt would be this:
- A user without permissions (left screenshot) starts the bot and tries to send the /terminal command to enable SSH (yellow). He also sends several commands to validate if he has access to the machine (green and blue), but the bot has not allowed terminal mode to be enabled.
- To the users in the whitelist it sends a message with the information (middle screenshot), warning that a user has started the bot (red).
- When the anonymous user sends the command /terminal (right screenshot), it will send us a message indicating that it has tried to execute a command (yellow), as well as resending us the command attempts (green and blue).
Comments