Deploying C2 malware pt.2 [2] - Flipper Zero BadUSB
Taking a step further from what we saw in the Havoc C2 post, let's take it a step further. Lets use the app BadUSB from Flipper Zero…

Taking a step further from what we saw in the Havoc C2 post, let's take it a step further. Lets use the app BadUSB from Flipper Zero…
You may have heard that ‘bad guys can connect to your computer to do bad things’, but how and why? There are actually many ways to infect…
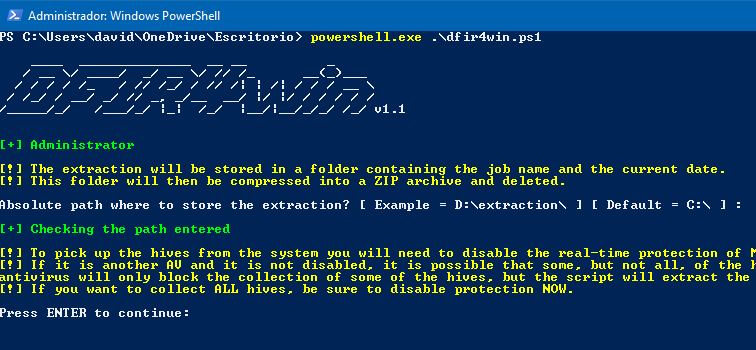
Manually extracting artefacts from an infected computer can sometimes be tedious with so much information to search for, documents and logs. That's why the less time it…